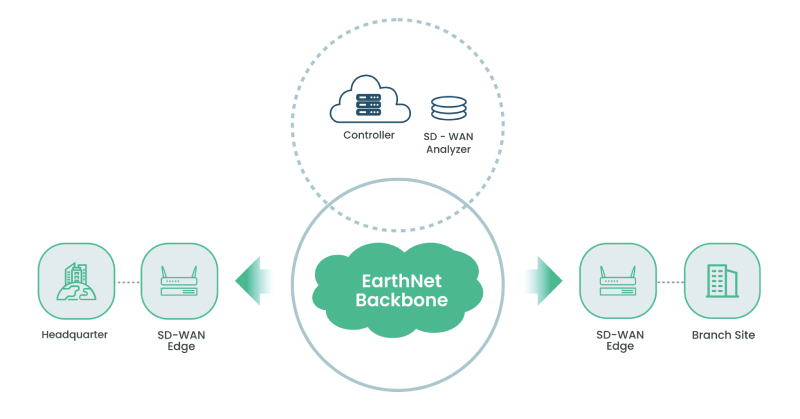
SD- Security
We provide users with high-performance, high-protection firewall services. Leveraging precise big data analytics, we enable automated attack tracing, attack protection, virus filtering, and behavior control—while delivering one-stop SASE (Secure Access Service Edge) solutions to customers.